Protect your software supply chain with YubiKeys and YubiHSMs
Learn how to leverage the YubiKey and YubiHSM to help enhance, streamline, and secure your software development practices. This guide is for developers, architects, and administrators looking to get the most out of their Yubico tools to improve their developer experience.
Protection for every stage of your software supply chain
After completing this guide, you'll have an understanding of some simple security techniques that can be used to harden the security around your application's development environment.
Often times these techniques are overlooked as they're seen to add friction to the developer experience. With Yubico's tools, you never have to sacrifice security for ease of use. By the end of this guide you'll understand how a one time setup can provide both a secure, and easy to use development environment.
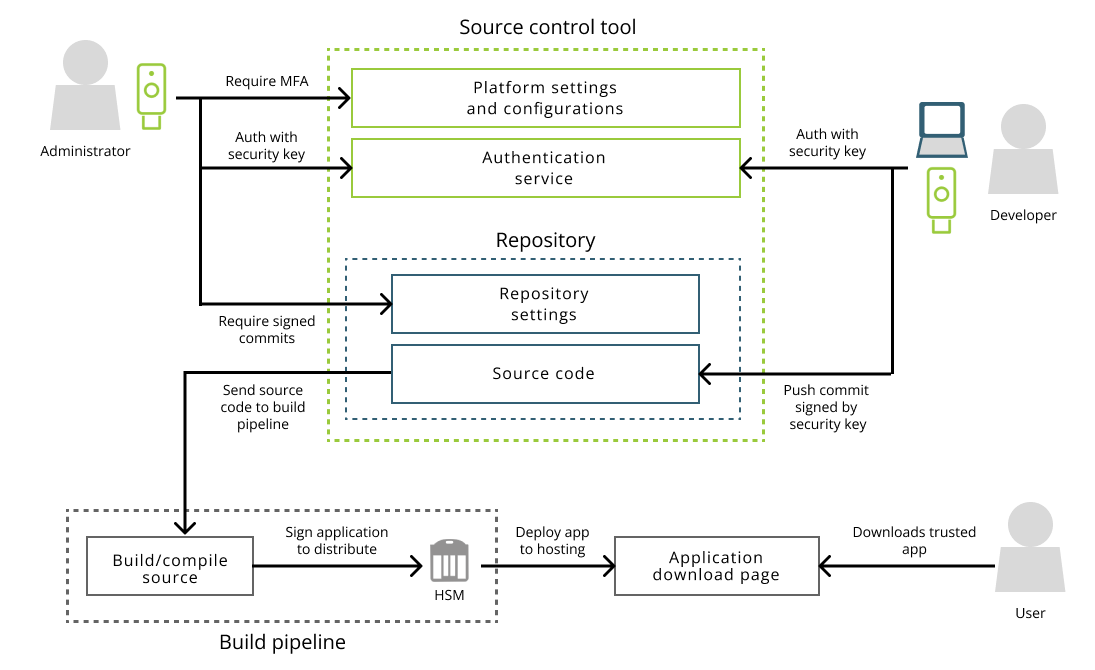
The graph below shows what a secure environment looks like between an organization's administrators, developers, and infrastructure that are all equipped with Yubico's security devices.
Set up your YubiKey for Git signing with FIDO2
One of the topics included in this guide is git signing with a YubiKey. See the video below to learn how easy it is to sign a commit with FIDO2. This guide includes a script that automatically generates and configures a signing key directly on your YubiKey